1. What are the most significant cyber threats currently targeting the asset management industry, and how are they evolving?
Cyber-attacks have become increasingly prevalent across all industries. Asset managers would be a particular target due to access to significant financial assets and sensitive client data. Current threats in our industry include sophisticated ransomware attacks, where sensitive data is encrypted by hackers who demand a substantial ransom while threatening to leak confidential client information to the public.
2. How can asset management firms effectively balance cybersecurity requirements with operational efficiency and client experience?
Balancing increasing compliance requirements with operational efficiency while ensuring an uncompromised client experience remains a challenge in the asset management industry. Firms also need to stay cognisant of the fact that while technological advancements can be leveraged for business efficiency and improved performance, they simultaneously pose significant threats to the protection of client assets and data.
The introduction of the FSCA and PA’s Joint Standard 2 of 2024 (Joint Standard), sets out the principles for cybersecurity and cyber resilience that South African financial institutions must comply with to achieve sound practices and processes in managing cybersecurity risk. In ensuring that cybersecurity and cyber resilience measures are commensurate with the nature, size and complexity of a particular organisation, as explained in the Joint Standard, firms should adopt a risk based approach to the management of cybersecurity.
Ideally, this approach should be regarded as a means to add value to the overall client experience, particularly as clients increasingly prioritise modernisation and accessibility across financial services.
The cornerstone of this balancing act is developing a comprehensive understanding of the firm’s existing cybersecurity landscape. This enables organisations to differentiate themselves through a unique value proposition while facilitating rapid gap identification and implementation of industry best practices.
Key activities that support this balance include mapping of IT related business processes, independent reviews of IT landscapes, identifying cybersecurity and cyber resilience gaps in systems and software, understanding how personal information is used and stored and detecting vulnerabilities in relation to third-party service providers. This will help firms identify risks and prioritises risk management efforts accordingly.
When a risk focused approach is followed, compliance can be integrated into operational processes more seamlessly, ensuring that cybersecurity measures serve to enhance and not impede business operations. Communication and involvement by all relevant stakeholders regarding compliance and operational objectives will be imperative.
3. How can asset management firms ensure their third party vendors and partners meet appropriate cybersecurity standards?
Outsourcing arrangements and the reliance on third party service providers exposes asset management firms to various risks, including inadequacy or inconsistency in approaches to cybersecurity and cyber resilience, ultimately leading to non-compliance.
To mitigate these risks, asset management firms should conduct due diligence investigations on the third party prior to an appointment. The due diligence should enable firms to establish and evaluate the cybersecurity and cyber resilience measures undertaken by the service provider and assess the extent of the cyber security risk that may be introduced.
Due diligence assessments should examine cyber security features including:
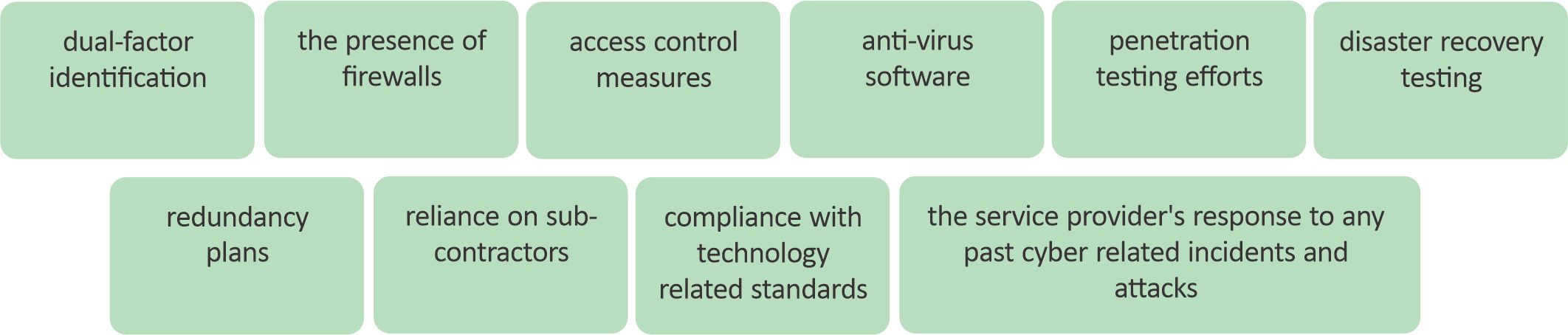
Given the dynamic nature of cyber risk firms should implement ongoing monitoring and robust oversight models to ensure continuous compliance. The monitoring frequency and depth should align with the criticality of the vendor relationship.
In addition, contractual agreements must include specific clauses addressing cybersecurity concerns such as compliance with relevant standards, reporting of cybersecurity breaches, data protection requirements and the consequences of non-compliance.
It is essential that criticality is established in line with the risk based approach to compliance envisaged in the Joint Standard. Monitoring efforts will range in accordance with the level of risk introduced by the use of each third party’s services and the extent of the firm’s reliance on the third party.
We believe asset managers should adopt a risk-based approach to cybersecurity, monitoring both technological and compliance requirements to ensure they remain resilient in a fast evolving landscape where data is under threat. It is important recognise the benefits of advancing technology and place a strong focus on balancing the adoption of automation in operational processes that allows more efficient delivery to clients with the compliance requirements that are critical to protect client data and financial assets.

